If you’re not running an employee advocacy program, you could be missing out on a lot of potential reach.
Why? Your employees are one of your biggest untapped marketing resources. They are the influencers and brand ambassadors who have been under your nose all along.
Sure, your employees are probably already posting about your workplace or brand without you asking. But an official employee advocacy program can help take that organic influence to the next level. Studies show that advocacy from your team can help shorten the sales cycle, attract and develop new business, and recruit top-tier talent. Plus, you can extend your organic reach by 200% and increase profitability by 23%.
Ninety-eight percent of employees are on social media anyways for personal use. Why not tap into their personal networks and benefit from their personal influence?
Read on to learn everything you need to know about kick-starting your own employee advocacy program.
Bonus: Download a free employee advocacy toolkit that shows you how to plan, launch, and grow a successful employee advocacy program for your organization.
What is employee advocacy?
Employee advocacy is when members of a workforce promote their company. This promotion can happen online or offline, but in 2023, the most common and effective way to do this is on social media. It’s like word-of-mouth for the digital age.
When employees practice social media advocacy, that means they’re sharing company content on their personal social media accounts. This includes everything from job postings to blog articles to industry resources to new product launches.
Proud to work at Salesforce, named one of the 2023 #WorldsMostEthicalCompanies by @ethisphere for the 14th time! https://t.co/YVBd98bepX
— Nicole Miller (@salesforceQueen) March 13, 2023
But employee advocacy on social media can also happen via original social media content.
If an employee shares a positive glimpse of your company culture, that also is advocacy in action. Think: an Instagram Story spotlighting your office Halloween jamboree, or a TikTok of the marketing team trying the Harlem Shake challenge 10 years too late, or a behind-the-scenes tour of how they’ve decorated their cubicle.
Whether they’re re-posting your brand’s content or crafting their own, any social media content that promotes your company can be considered employee advocacy.
Digital employee advocacy can happen organically (we see you, super-loyal keeners!) but if you can formalize the process and parameters of what and how your team shares brand-related content, your company will see even more benefits.
Why is employee advocacy important?
Your employees are already on social media. Is Joe in Accounting’s mom your target audience? Maybe not. But it’s likely Joe has many followers who are, or who can at least help spread your message.
And social media is now a top channel for online brand research, second only to search engines. Customers rely on social media at every stage of the purchasing journey.
An employee advocate’s positive post about your brand can really help you stand out from the crowd.
Employee advocacy can benefit companies in three ways:
- It positively impacts sales due to increased brand awareness and favorable perceptions (“brand sentiment”).
- It improves staff recruitment, retention, and engagement.
- It aids in PR crises and issues management.
Why does employee advocacy work so well? It’s all about trust.
Trust is more influential than love when it comes to choosing to buy from a brand or not. As Edelman puts it, “Trust is the ultimate currency.” Fifty-nine percent of consumers will stop buying from a company if they don’t trust the brand.
Building trust starts, of course, with behaving consistently, following your brand values, and trying your best not to get caught up in some sort of ethics scandal. But beyond being on your best behavior, having the endorsement of trustworthy people goes a long, long way.
No one asked radio host Shiva Reddy to post a video of the CBC newsroom on Instagram, but she did anyway. This quick, visual love letter to her place of work gives her friends and followers a sense that this is a company to root for.
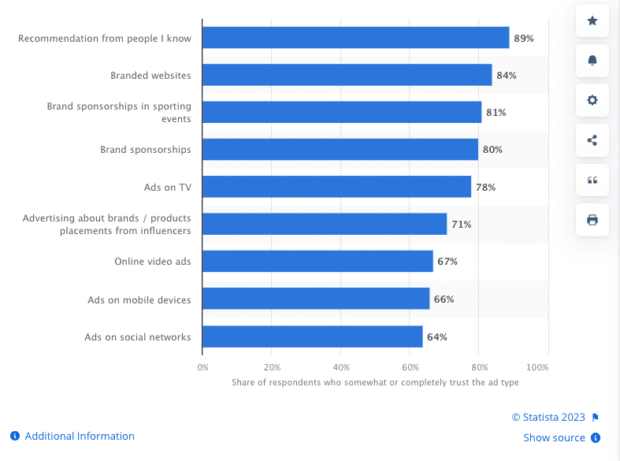
Eighty-nine percent of consumers trust recommendations from people they know over branded content or traditional ads. Fifty-six percent of Millennial and Gen Z consumers trust influencers more than brands. So it’s probably worth your while to spend less time finessing the perfect social media ad and more time encouraging your amazing crew of potential ambassadors to spread the word to their followers.
Hootsuite’s research shows employee advocacy on social networks is directly related to higher brand health metrics, including positive sentiment, value, and share of voice—especially among mature organizations.
For sales or recruitment teams, a successful employee advocacy program can be a great basis for social selling. Employees can also enhance their credibility and position themselves as industry experts.
Georgia State University implemented a #TheStateWay hashtag campaign to encourage students and employees to share news, insights, and stories. The result? 26,000 social shares and millions of impressions (and counting). Everyone from proud parents to campus groups can show off their Panther Pride, allowing the university to achieve a wide-ranging, organic reach.
PS: Georgia State also used Hootsuite Amplify, our employee advocacy tool, to help make re-sharing social media content created with this hashtag quick and easy for faculty and staff.
Okay, okay! You’re convinced! You’re ready to build your employee advocacy program on social media! Good news: the very next section here is going to show you how.
Here’s how to build an employee advocacy program on social media.
Step 1: Create a positive and engaged workplace culture
If your employees don’t love working for you, they’re not going to be motivated to post about you on social media. (Or if they are posting, it’s probably not the kind of content you would want anyone to see.)
The two key motivators for an employee to want to become an advocate are:
- A positive relationship with the organization
- Strategic internal communication
We’ll focus on the first point to start.
It’s a win-win situation: Happy employees want to share about their company, and those who share about their company—and get rewarded for it—become even happier employees. (We’ll cover reward ideas in the last step!)
Search for the #sephoralife hashtag, for instance, and you’ll find photo after photo of smiling Sephora employees. (If there’s someone out there working the makeup counter who isn’t having a blast, they’re probably just quietly plotting their resignation letter.)
So how do you create an engaged workplace culture?
Research from Gallup suggests some of the main factors influencing engagement are:
- Having a mission and purpose
- Knowing what’s expected
- Having the materials and equipment to do your job best
- Receiving recognition
- Having someone to care about your accomplishments and encourage your development
- Feeling like your opinions are heard
They’re all pretty big-picture concepts. Notice that they all have more to do with self-worth than whether or not the company has a ping-pong table.
Many, many books exist about creating great workplace cultures (in much more detail than we could hope to capture here), but Gallup’s research suggests that 70% of employee engagement is determined by the manager. So, start there.
Leaders need to clearly define manager roles and expectations, provide training and tools to help those managers get there, and create evaluation processes that help employees thrive.
Of course, creating a great place to work has many other benefits besides encouraging employee advocacy. Research points to engaged employees resulting in higher profitability (+23%), customer loyalty (+10%), and productivity (+18%).
Step 2: Set goals and KPIs for your employee advocacy program
Before asking your employees to post about your company, it’s important to figure out why you’re even asking them.
Setting goals and communicating them to your employees eliminates ambiguity and gives you measurable social media metrics to track progress.
Example goals for your employee advocacy program could be acquiring more leads, recruiting talent, improving brand awareness, or increasing share of voice on social.
Some key KPIs to track are:
- Top contributors: Which individuals or teams are sharing the most? Which advocates are generating the most engagement?
- Organic reach: How many people see the content shared through your employee advocates? (Psst: try our employee advocacy calculator to calculate your potential reach.)
- Engagement: Are people clicking links, leaving comments, and re-sharing content from your advocates? What is the engagement per network?
- Traffic: How much traffic did the content shared by employee advocates drive to your website?
- Brand sentiment: How has your advocacy campaign impacted your overall brand sentiment on social media?
Also, be sure to track mentions of your company hashtag if you create one. Giving employees a hashtag to mention can help with recruitment and brand sentiment goals by showing off your company culture. It can also help employees feel more connected to the company and each other.
Step 3: Identify employee advocacy leaders
While it may be tempting to pick your executive team as leaders of your employee advocacy program, the real leaders of your social media advocacy program should be the people who are already social-media all-stars.
Instead of focusing on title or rank, focus on who naturally uses social media:
- Who is developing a personal brand using social media?
- Who naturally shares industry content?
- Who is the public face of your company, either in their role (speaking engagements, PR, etc.) or number of social media connections?
- Who is enthusiastic about your industry and the company?
Empower these people to help build your employee advocacy program. Engage them in defining and communicating campaigns, setting goals, and creating incentives. They’ll help you learn what kinds of tools and resources employees are most likely to use and share. They’re on the front lines already, after all! Trust their expertise.
Then, work with your advocacy leaders to identify potential beta testers before launching your program company-wide. They can help guide your employee advocacy strategy and provide honest feedback.
You may see an initial flurry of social shares when you launch your employee advocacy program. But without effective internal leadership, this enthusiasm will fizzle out over time. Employee advocacy leaders help make sure advocacy is an ongoing focus.
Step 4: Establish employee social media guidelines
Employees need to know not just what the message is, but also the best way to communicate it. What kind of language should they use? How often should they post? How should they respond to comments?
To address this, you need two documents:
- Social media content policy: A “do’s and don’ts” of what employees should share, topics to avoid (e.g., politics, etc.), answers they can provide to common questions (FAQ), and more.
- Brand style guidelines: This is the visual guide, including how to use the company logo, unique terms or spelling your company uses (e.g., it’s Hootsuite, not HootSuite!), hashtags to include, and more.
Guidelines, especially content ones, aren’t meant to police your employees. You don’t want to create such a long list of “don’ts” that people are too scared to share anything at all, in fear of losing their job. With the right guidelines clearly stating what’s off-limits while allowing for authentic expression, you eliminate that fear (and avoid a potential PR nightmare or a wrongful dismissal lawsuit).
Clear guidelines also help protect your company’s reputation and avoid security risks. Some guidelines are common sense—for instance, avoiding vulgar or disrespectful language or sharing confidential information. Other guidelines may need input from the legal department.
Make sure the guidelines are easy to understand and follow. It shouldn’t be a boring, 50-page, all-text document. Include visual examples and recommendations on what, where, and how to share.
(Also include contact information for your advocacy program’s leader so employees know who to ask for additional guidance if needed.)
We’ve got a free template for you to create an employee social media policy or check out examples from other companies.
For examples specific to your industry, try searching for “employee social media policy” + (a company name or your industry):
Step 5: Get employees involved in your strategy
Once you have goals and guidelines in place, it’s time to reach out to employees. Let them know about your advocacy program and tools, and then set ‘em loose on the world!
Of course, you should never force employees to share brand content on their personal channels. (If you’re saying, “Talk about us on Snapchat, or else!” it’s time to take a long, hard look in the mirror.)
Instead, involve your employees in content planning. Share your current social media strategy and ask them which types of content would show off the company culture or what would fit in with the goals of your employee advocacy program.
We’ll cover more about content below, but use the feedback your teams give you to guide your overall strategy. For example, Hootsuite’s employee advocacy program’s content categories are internal announcements, product announcements, thought leadership, and recruitment.
Step 6: Create valuable resources for employees to share
The real key to getting your employees to share? Provide them content they need to either make their job easier or help position them as an industry expert.
Research from LinkedIn shows users who share advocacy content receive 600% more profile views and grow their networks three times faster.
Ask your employees what questions customers are asking them. If 10% of new leads are asking a seemingly boring accounting question, well, so be it: Time to create a seemingly boring but effective piece of content about accounting.
If it’s what your customers want, it’s worth it. Your employees on the front lines know what customers want. Create content serving that, and your employees will be happy to share it.
When financial institution Julius Baer started its advocacy program, it reached out to a content partner to create custom advocacy content for employees to share. With the help of that partner, they create five content pieces a week for employees to share, primarily evergreen content. It’s been a successful project: more than 350 of the 500 registered employee users post regularly.
Pro tip: Create and regularly update a content library of these types of evergreen content resources so employees can find them easily.
Additionally, don’t forget about the power of a personal message. Pre-approved content is great for quick shares, but give your employees the freedom to write their own captions for image or video posts, too (as long as they follow your brand guidelines).
For example, 32% of all Hootsuite employee advocates shared about our “Wellness Week,” where our entire company took a week off to recharge. The result? 440,000 organic impressions from brand advocacy in a single week.
Hootsuite employees around the globe will be logging off for a week without interruption in July! ✨
Check out all of Hootsuite’s new employee mental wellness initiatives here: https://t.co/mr4d0ued3Q #HootsuiteLife pic.twitter.com/DDJsY8cW6o
— braydencohen (@beingbrayden) May 27, 2021
Ask employees to share their favorite feature about a new product or how a recent company policy positively impacted them. Creating their own unique content will resonate more with their followers. That’s important because those followers know your employee more than they know your brand (for now).
Once again, it comes down to having a culture great enough to make your employees want to share.
Step 7: Reward employees for their advocacy
Since you’re asking something from your employees, it’s only fair to offer something in return.
Educate employees on the benefits for them, like increasing their visibility and credibility as subject matter experts. But rewards should go beyond exposure: tangible incentives like gift cards or prizes can help employees feel like they have a stake in the program.
Many brands make social media advocacy into a game or contest.
For example, create a hashtag to promote a specific employee advocacy campaign. Then, create a leaderboard to show who’s getting the most impressions or engagement for the hashtag. Gift a prize to the winner, or for a more fair chance for everyone, put everyone who shared the campaign into a draw.
Other tactics you can apply to sweeten the deal include:
- VIP programs
- Development opportunities
- Early access
- Badges
- Challenges for teams or individuals
Learn more about how to roll out an employee advocacy program with our program guide (click below to download).
Bonus: Download a free employee advocacy toolkit that shows you how to plan, launch, and grow a successful employee advocacy program for your organization.
Employee advocacy best practices
Only share engaging content
Sorry if we sound repetitive, but this one is important! Explore our cheat sheet for engaging social media content here if you’re having trouble coming up with ideas.
Make it worth your employees’ while
Offer content that helps your employees build their online image as industry experts. And make your entire employee advocacy program fun to participate in.
Find what motivates your team and do it. Prizes? Contests? Random gift cards just to say thanks? After all, your employees are giving you tons of free organic reach. The least you could do is buy ‘em a coffee card once in a blue moon.
Foster a great company culture
Engaging in employee advocacy—and with their role and your company in general—comes from naturally wanting to share and being proud of where they work. Give them good reasons to be proud.
Measure success
An advocacy program should align with your organization’s primary business goals and inform the metrics you should be tracking. The worksheet provided earlier sets the framework for you to measure the success of this program. You don’t want to forget about measuring its shortcomings as well. These will give you valuable insights that will improve it and keep it rolling in the future.
Perhaps you will use a scorecard that ties back to your objectives. Decide how often you’ll measure. Will it be weekly, quarterly, yearly?
Make sure you set your benchmarks and identify trends and variations from there.
FAQs about employee advocacy
What is an example of employee advocacy?
Employee advocacy happens when a team member shares content about your company, whether online or offline—for example, a social media post about your brand, shared by someone who works for you.
To get more specific, maybe they’re showcasing their favorite products from your new line of dog ponchos on Instagram! Maybe they’re re-posting a job listing for a new Executive Assistant/Barista! Maybe they’re live-streaming their experience at the big industry conference in glamorous downtown Omaha!
Basically, any time your employee posts positive content about your company or their experience working for you, this is employee advocacy in action.
Why do we need employee advocacy?
Employee advocacy benefits companies by positively impacting sales due to increased brand awareness and favorable perceptions (“brand sentiment”). It also improves staff recruitment, retention, and engagement. Employee advocacy can also aid in PR crises and issues management.
HootsuiteAmplify — your employee advocacy platform
The hardest part of employee advocacy is often the execution. Where will they find content to share? Where can they review your social media and brand guideline documents? How will they find out about new content?
You can go as basic as having everyone sign up for the company newsletter to find content to share on their own, or… Use a done-for-you employee advocacy platform to distribute approved content, easily share to their profiles with one click, and seamlessly measure the ROI and results.
Hootsuite Amplify is your all-in-one solution for setting up an employee advocacy program people want to be part of. Check out how it works in under two minutes:
https://youtu.be/72RqbLHccyY
If you already use Hootsuite for social media planning, it’s as easy as adding the Amplify app to your account (for Business and Enterprise customers). Boom, done!
Having a central hub that employees can visit to stay informed and easily share pre-approved content from pays off. At Hootsuite, we have a 94% adoption rate for our employee advocacy program and a 64% share rate. Our program earns over 4.1 million organic impressions per quarter!
Plus, Amplify analytics reports allow you to track program growth and content performance metrics—and measure its ROI along with all your other social media metrics in your Hootsuite account.
Tap into the power of employee advocacy with Hootsuite Amplify. Increase reach, keep employees engaged, and measure results—safely and securely. Learn how Amplify can help grow your organization today.
Request a demo of Hootsuite Amplify
Hootsuite Amplify makes it easy for your employees to safely share your content with their followers—boosting your reach on social media. Book a personalized, no-pressure demo to see it in action.
Book your demo now